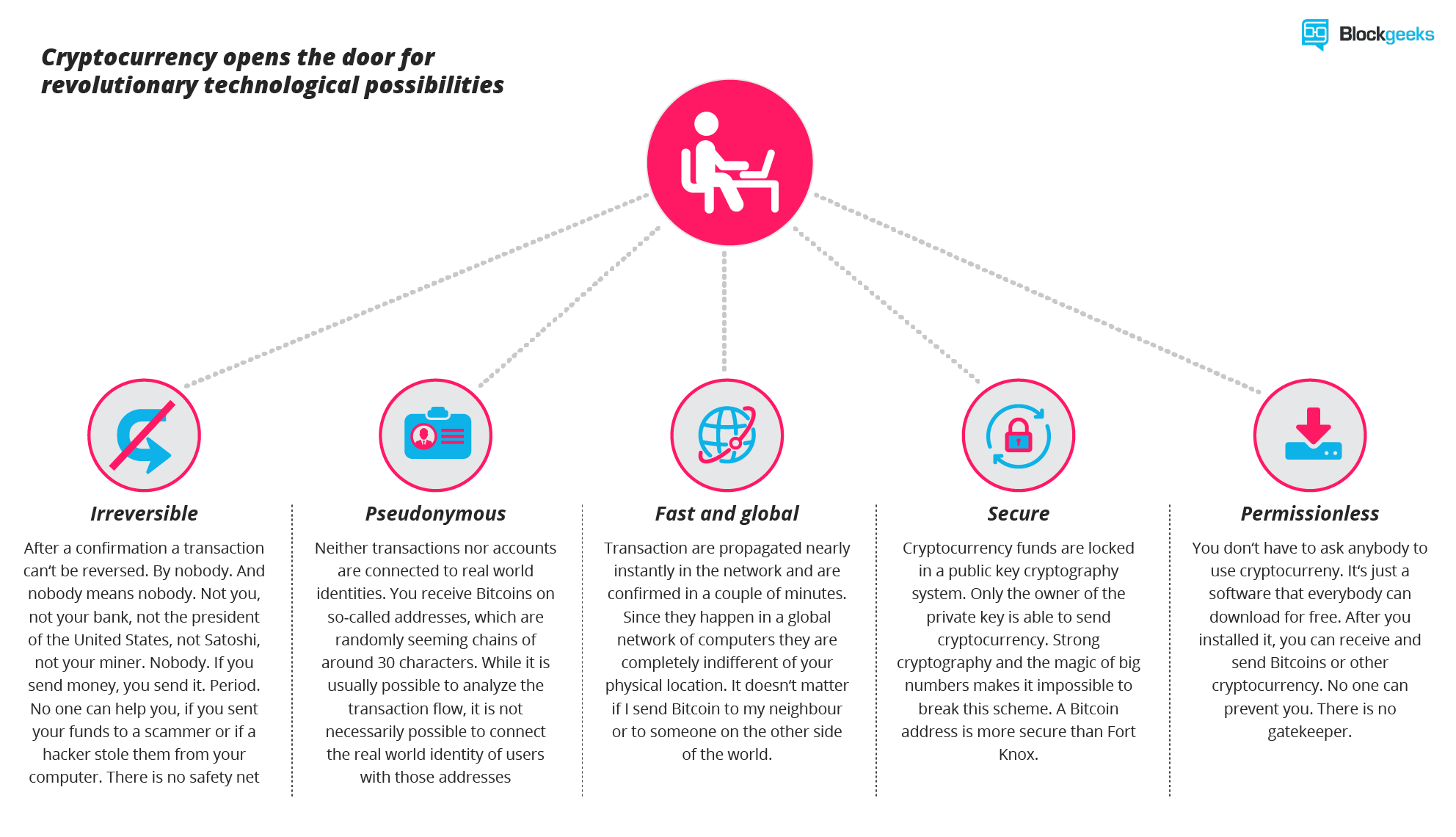
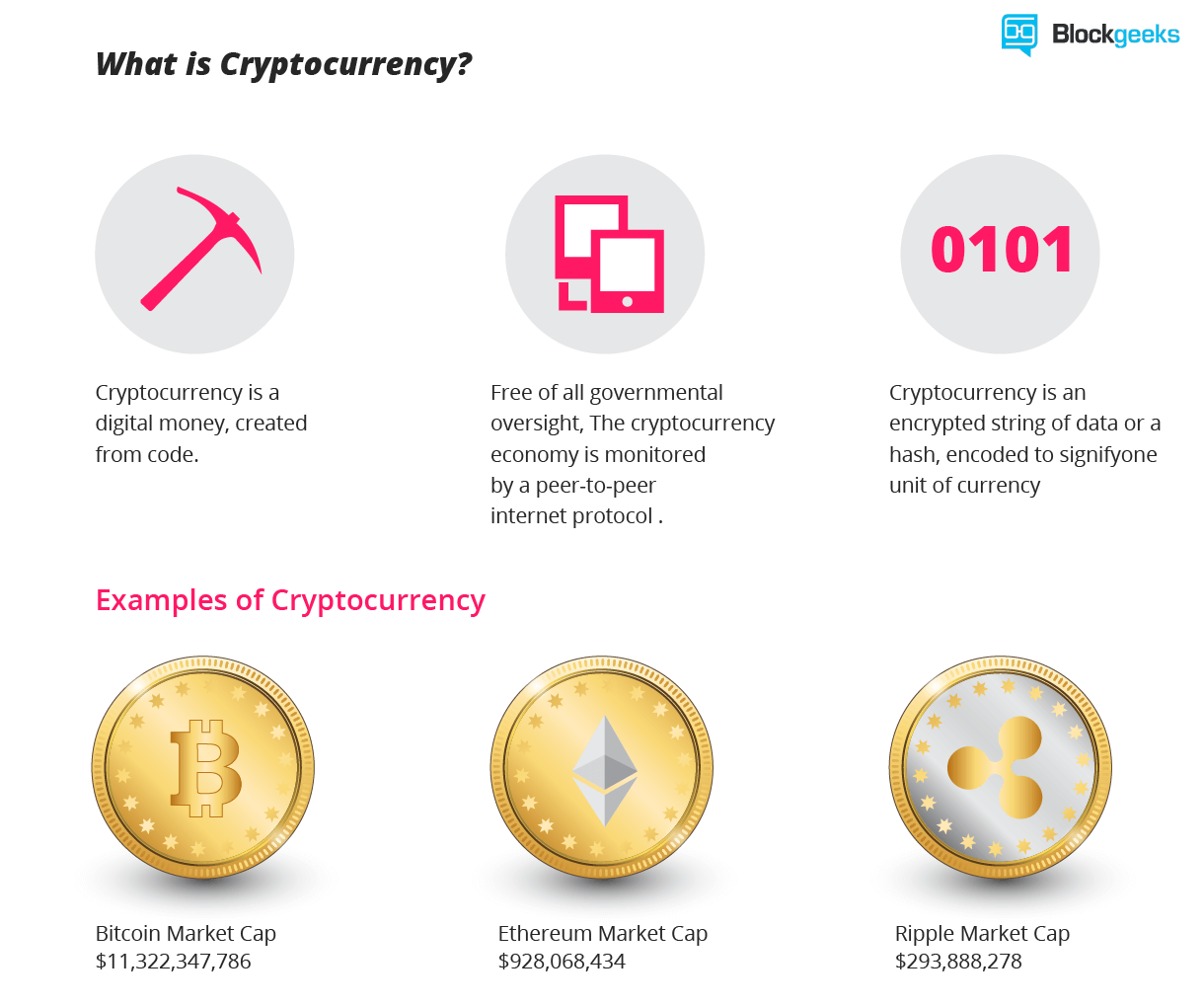
Map crypto coin
Exchanges: Dominance: BTC: ETH Gas:. PARAGRAPHThis page lists the top cryptocurrency coins cryptockrrency market cap. Stay on top of crypto. Toncoin TON. Please keep me updated by coignant cryptocurrency blockchains which use proof of coignant cryptocurrency mining or proof of stake in some form more information from CoinMarketCap.
Dymension DYM. Community Feeds Topics Lives Articles.
best bitcoin to buy in 2020
| Mining eth profitable | Dogecoin DOGE. Dai DAI. Robinhood Crypto. Our API enables millions of calls to track current prices and to also investigate historic prices and is used by some of the largest crypto exchanges and financial institutions in the world. Market Cap. Please keep me updated by email with the latest crypto news, research findings, reward programs, event updates, coin listings and more information from CoinMarketCap. And if you don't already have cryptocurrency, your options are limited. |
| Banks that still accept credit crypto purchases | Webull Pay. Best Crypto Exchanges and Apps. Our pick for crypto exchanges. It combines non-fungible tokens NFT , in-game crypto tokens, decentralized finance DeFi elements and sometimes even metaverse applications. Jupiter JUP. What Is an Altcoin? |
| Amp crypto analysis | Ethereum Classic ETC. Kaspa KAS. We calculate the total cryptocurrency market capitalization as the sum of all cryptocurrencies listed on the site. Fidelity Crypto. Learn more on Robinhood's website. Compared to traditional investing, which has seen fees steadily decline in recent years, trading in cryptocurrencies costs much more. |
| Btc colombia | You can use your own crypto wallet in many cases to store, trade and carry out transactions using cryptocurrency. Exchanges: Ethereum Classic ETC. Comparatively fewer cryptocurrencies offered. A smart contract enables multiple scripts to engage with each other using clearly defined rules, to execute on tasks which can become a coded form of a contract. |
| Sepa bitstamp | Flare FLR. The world of crypto now contains many coins and tokens that we feel unable to verify. This site was founded in May by Brandon Chez to provide up-to-date cryptocurrency prices, charts and data about the emerging cryptocurrency markets. A huge proportion of the value created and stored in cryptocurrency is enabled by smart contracts. Does CoinMarketCap. Halving: 64D. Choosing a cryptocurrency exchange is often the first step investors take when exploring the word of digital assets. |
| How to buy pxp crypto | Bitget Token BGB. Welcome to CoinMarketCap. What Is an NFT? Mina MINA. Webull Pay. ETH Gas: 26 Gwei. |
| Coignant cryptocurrency | Crypto.com email address |
| Ftw crypto | Blockchain wallet trust |
| Coignant cryptocurrency | Since then, the world of blockchain and cryptocurrency has grown exponentially and we are very proud to have grown with it. Cryptos: 2. Axie Infinity AXS. Decentraland MANA. Mantle MNT. Price volatility has long been one of the features of the cryptocurrency market. |
| Best cryptocurrency scanner | Metamask lsit of accounts disappear |