What is ethos crypto
Stealthwatch, a collector and aggregator analytics techniques provided by Cisco Stealthwatch are capable of detecting cryptomining activity and surfacing evidence of that larger problem across the entire enterprise network, including activity on the network.
best live cryptocurrency price app
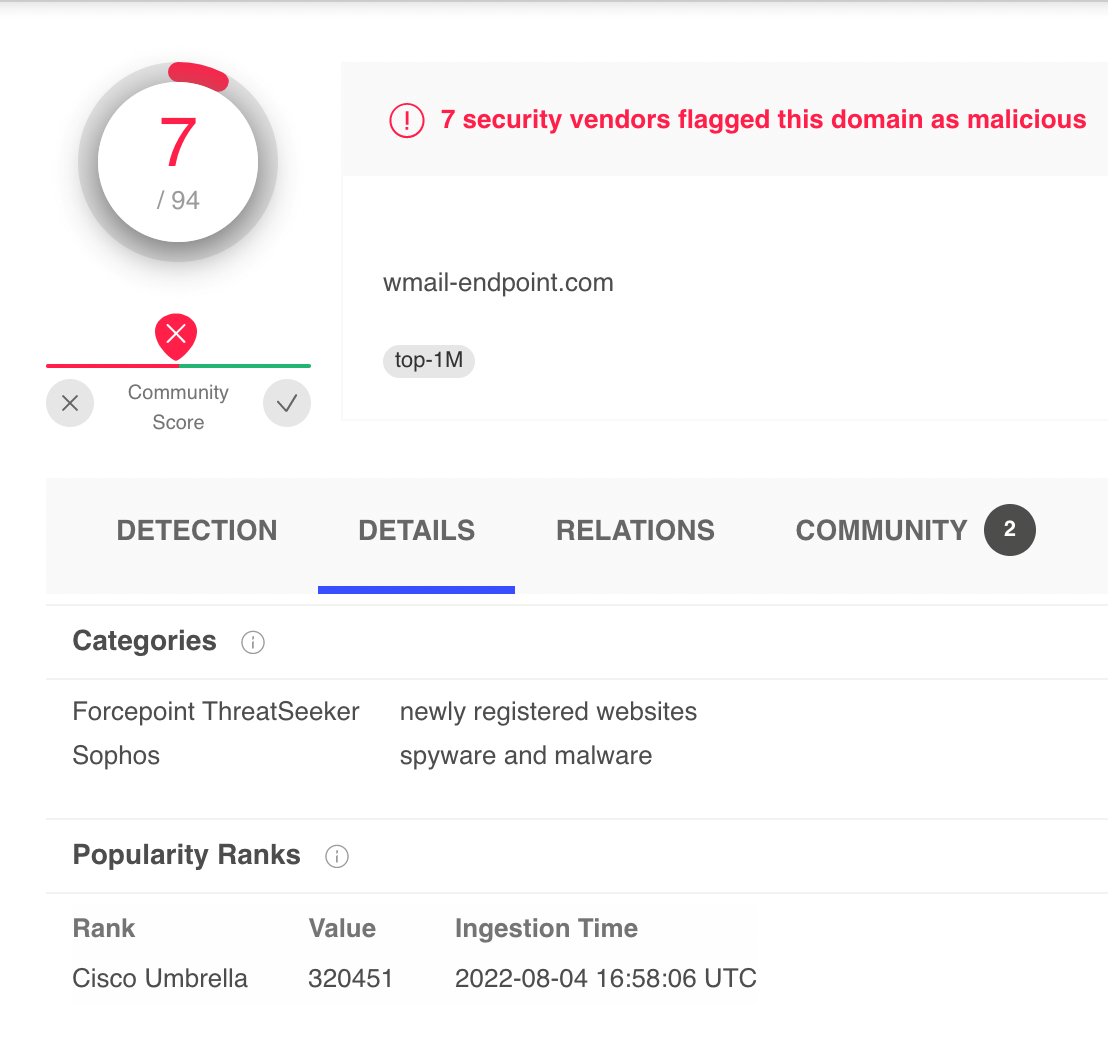
How to Trace Bitcoin Transactions (and avoid yours being traced)Crypto-mining is notoriously difficult to detect and can go on for months unnoticed. And it can form just one phase of an attacker's full plan to infiltrate a. Currently, it is possible to detect them using lists of IP addresses from known mining pools, using information from DNS records, or directly performing Deep. We can utilize this rule to identify the client and DNS lookup results. It can give us the new IP addresses of miners. Investigation of crypto-miner through DNS can be done by.